Safeguard Your IIoT Solution from the Inside Out
September 7, 2018

A traditional way for solution developers to guarantee the optimal performance of their systems is to take an “outside in” approach. This includes implementing firewalls and other gating systems to keep unauthorized users out, creating secure connections to external systems and data stores, and enforcing physical access policies to address how people interact with solution components. They might also overlay tracking or management applications that assess performance and security by observing system behavior or sniffing through log files. But as the footprint of distributed IIoT systems and their complexity increase, this approach alone may not be sufficient. It may be time to turn this approach on its head and look at the benefits of adding trust from the inside out.
A Critical Function for IIoT Devices: Data Collection
Let’s zoom in to the very basics of an IIoT system to examine why this might be the case. An IIoT system is implemented to provide insights about the workings of an existing physical system, collecting data that enables users to make smarter business decisions. For example, this could include performing preventive maintenance at times that both maximize production uptime while minimizing unexpected failures in the case of a smart manufacturing system or for tracking or optimizing asset utilization in a logistics system.
Many of these innovative solutions depend on the installation of IIoT devices like cameras or external sensors into existing environments, in addition to leveraging the data from embedded sensors and tracking technology. These devices are often small and while unobtrusive, may be vulnerable to unintended access or movements, even if accidental. So an intrinsic method for ensuring the trustworthiness of the device — both its security and its accurate operation — may be an essential component of a successful system.
What do we mean by intrinsic methods? And what are their advantages?
An Intrinsic Solution Defined
An intrinsic solution for IIoT devices and systems is a small software application that can reside on the device itself, with the following benefits:
- Hacking or Intrusion Prevention
Detecting malicious connections such as unauthorized USB connections, new software installations, and the like, and providing immediate notification to system operators - Tamper-resistance
Observing changes to device orientation or environment that might impair or prevent accurate data collection - Reliability
Monitoring system performance, state, and operating conditions at the source - Data Assurance
Validating and tagging data as it’s collected; tags will remain with the data packets throughout their lifecycle.
You may think that protections at this level aren’t necessary for your system because it’s housed entirely in an access-controlled environment. But even accidental jostling can impinge on the quality of your data collection. And if cameras are meant to track any physical activities, even if anonymized, the lure of simply turning the camera around may be just too great for some workers to resist.
An Important Perspective for Device Makers
This “inside out” approach is not only important for system designers. As recommended by TechRepublic, among others, the number 1 approach for building secure IoT devices is to “build security into the devices from the beginning”. So it’s imperative that device manufacturers are taking this approach as well.
Trust is best established by first-hand knowledge, whether it’s trust in another person or trust in the way a system performs. Why settle for second-hand referrals or inferred information when it comes to trusting the reliability of your critical business infrastructure?
Establish verifiable Trust from the inside out.
Interested in understanding more about how to ensure your IIoT data operations are delivering maximum value? Read our latest white paper “Data Reliability in the Smart Factory Environment”.
Related articles
We were very excited to learn on Friday that the Corlina System of Trust has received a 2019 IoT Evolution Industrial IoT Product of the Year Award from IoT Evolution World, the leading magazine and Web site covering IoT technologies. It’s very exciting when your product receives this type of
In our recent articles, we’ve talked about taking a different approach to embarking on building IIoT capabilities, one that protects organizations from pilot purgatory by focusing on a specific challenge in the manufacturing environment and yielding ROI quickly. It’s not a rip-and-replace method requiring massive investments in new equipment. It’s
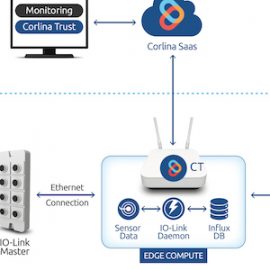
Solution Overview Corlina’s brownfield monitoring solution blueprint is intended to enable monitoring and decision-making based on information captured from already-in-place equipment. These existing systems are often implemented on closed architectures and/or closed data buses for reliability reasons, or they may not include any embedded sensors whatsoever. Corlina provides a cost-effective